Kaspersky Industrial CyberSecurity Platform
Native Extended Detection and Response (XDR) platform for critical infrastructure protection. The core of the OT cybersecurity ecosystem.
Overview
With the advent of hacktivism and targeted cyber-aggression, choosing a trusted partner with extensive experience and knowledge in the field of industrial cybersecurity has become one of the top priorities for industry leaders and developing companies alike. Establishing secure and extensive protection for industrial systems – including industrial control and automation systems (IACS) and supervisory control and data acquisition systems (SCADA) – is now one of the most important conditions for ensuring stable and successful operations for any enterprise.
Kaspersky Industrial CyberSecurity is a native Extended Detection and Response (EDR) platform for comprehensive protection of industrial enterprises and critical infrastructure. Without impacting on technological processes or system availability, it protects critical modern and legacy OT assets, automaton systems, and Ethernet-based industrial networks.
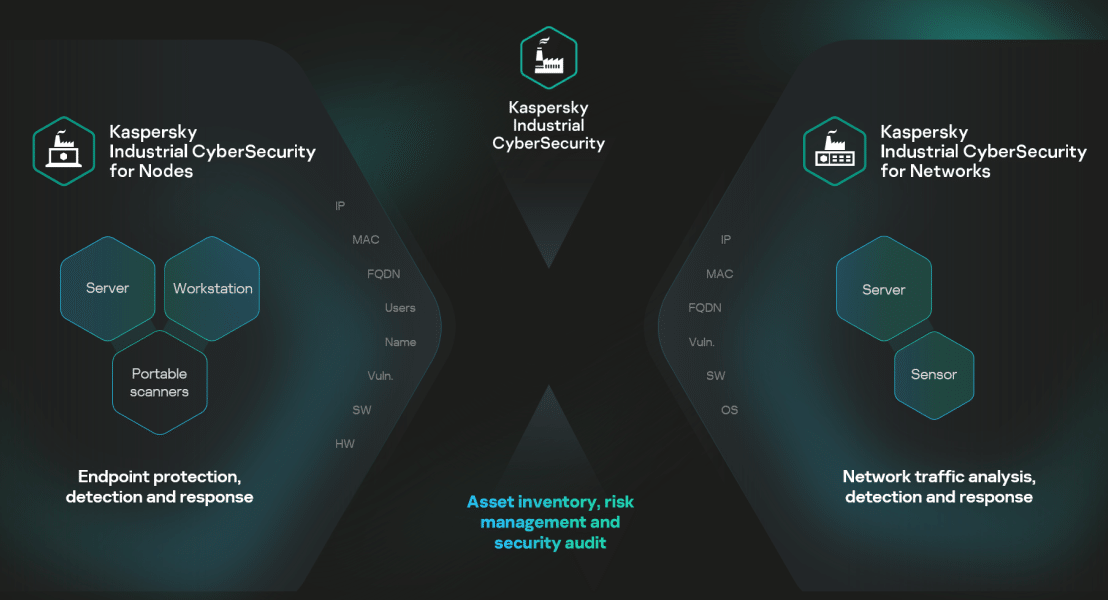
Platform components
KICS Platform
Native XDR platform for industrial enterprises, created and certified to protect modern and legacy OT equipment and networks from cyber-initiated threats. The platform consists of integrated technologies that secure all components of Industrial Automation and Control Systems (IACS).
KICS for Networks
A flexible device-agnostic OT network traffic analysis, detection and response product. It acts as a site-level central server within the platform.

KICS for Nodes
An industrial-grade product offering low-impact endpoint protection, detection and response for Linux and Windows environments. It acts as an endpoint sensor within the platform.
Key features

Network traffic analysis, detection and response

Endpoint protection, detection and response

Audit, risk and vulnerability assessment

Asset management

Network visibility

Development vectors
Key benefits

Certification
Creating safe, secure environments requires a joint effort, which is why Kaspersky increasingly collaborates with industrial automation vendors. We conduct certification and interoperability tests, prepare reference models, and integrate our diverse products and solutions. We provide mature, well-tested tools to help construct fault-tolerant, secure industrial systems.
- 137 certified systems from 55 vendors
- 12 national and international certificates

Custom solutions for every situation
Get specialized protection where you need it most
Kaspersky Extended Detection and Response (XDR)
A single point of management for all Kaspersky products, fostering open and comprehensive integration of business technologies, feeds, and controls within a unified environment and unlocking IT-OT convergence.

IT cybersecurity
Kaspersky’s Enterprise Portfolio reflects the security demands of today’s businesses, responding to the needs of organizations at different levels of maturity through a stage-by-stage approach.

OT cybersecurity
Kaspersky OT CyberSecurity is an ecosystem of technologies, knowledge, and expertise that protects industrial enterprises at every level. It offers a unified vision of comprehensive protection for industrial enterprises.

Kaspersky Industrial Cybersecurity Conference
Hundreds of experts attend the event every year to participate in roundtables, and share cybersecurity insights and best practices. Learn everything there is to know from previous conferences in our archive, and join us in 2024.